How To Hack Android Phone With Text Messages

Own an Android phone? Beware, Your Android smartphones tin can be hacked by just a malformed text message.
Security researchers have found that 95% of Android devices running version 2.2 to 5.1 of operating system, which includes Lollipop and KitKat, are vulnerable to a security bug, affecting more than 950 Million Android smartphones and tablets.
About all Android smart devices bachelor today are open up to set on that could allow hackers to access the vulnerable device without the owners beingness enlightened of it, according to Joshua Drake, vice president of platform research and exploitation at security firm Zimperium.

The vulnerability actually resides in a core Android component called " Stagefright ," a multimedia playback library used by Android to process, record and play multimedia files such as PDFs.
A Text Message Received...Your Game is Over
The sad news for most of the Android users is that the fix will non aid Millions of Android users that owned older versions of the operating organization that Google no longer supports, opening doors for hackers to perform Stagefright attack.
Drake has developed and published a scary exploit that uses a peculiarly crafted text message using the multimedia message (MMS) format.
All a hacker needs is the telephone number of the victim's Android device. The hacker could so sends the malicious message that will surreptitiously execute malicious code on the vulnerable device with no end user activity, no indication, zippo required.
"These vulnerabilities are extremely dangerous because they exercise not require that the victim accept any activity to be exploited," reads the Zimperium blog post published Monday.
"Unlike spear-phishing, where the victim needs to open up a PDF file or a link sent by the attacker, this vulnerability can be triggered while you slumber. Earlier you wake up, the assaulter volition remove whatsoever signs of the device being compromised, and you will keep your twenty-four hour period as usual—with a trojaned telephone."
Stagefright: Scary Code in the Middle of Android
The aforementioned vulnerability tin too be exploited using other assault techniques, such as luring victims to malicious websites.
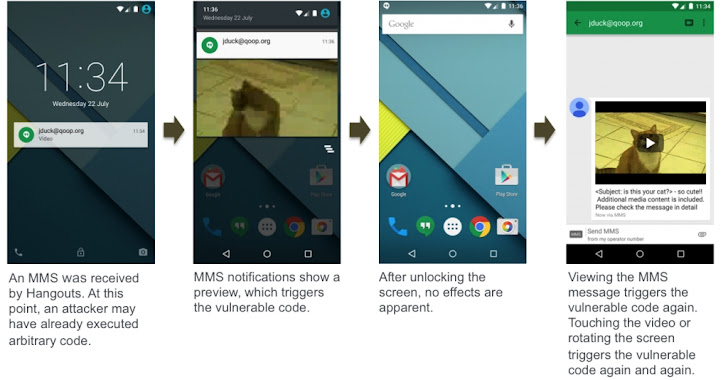
Drake will present his full findings, including six boosted attack techniques to exploit the vulnerability, at Black Lid security conference in Las Vegas on on Baronial five and DEF CON 23 on Baronial 7, where he is scheduled to deliver a talk titled, Stagefright: Scary Code in the Heart of Android.
Well-nigh all Android devices containing Stagefright are in question. Co-ordinate to Drake, all versions of Android devices after and including version 2.2 of the operating system are potentially vulnerable, and it is up to each device manufacturer to patch the devices against Stagefright attack.
When volition I expect a Fix?
Google has patched the code and sent it to device manufacturers, only devices require over-the-air updates from companies such as Samsung or Motorola to update their customers' phones.
Given the shaky history of handset manufacturers and carriers rolling out security patches, it is not known how long the companies volition take to update vulnerable Android devices against Stagefright attack.
However, Silent Circle has patched the issue in its Blackphone, as has Mozilla, which uses Stagefright code in Firefox OS.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
How To Hack Android Phone With Text Messages,
Source: https://thehackernews.com/2015/07/android-phone-hacking.html
Posted by: scottgasked.blogspot.com


0 Response to "How To Hack Android Phone With Text Messages"
Post a Comment